Improving the security of medical devices
-
A look from the external interfaces
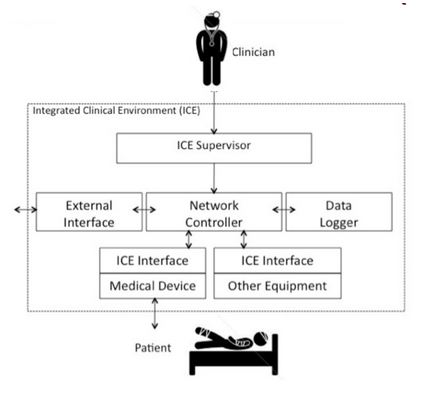
Improving the security of integrated clinical environment communication protocols
To improve patient care in clinical environments, it is critical to have secure protocols between connected devices. Such a network would provide better resilience against accidental privacy leaks and active attacks. The first part of our project looked at improving the security of integrated clinical environments by assessing the suitability of current clinical communication protocols from a security perspective. Many gaps were identified, and a path to strengthen those protocols was set. We are now working on applying known methods to the current protocols, which would greatly improve the picture. The next step will be to develop new mechanisms that address specific requirements in the next generation of integrated clinical environments.
Key security requirements for integrated clinical environments:
Secure medium access control: An attacker with access to the wired or wireless medium should not be able to generate forged layer 2 protocol messages that would be accepted by a receiving interface. Confidentiality may be added as needed.
Secure sessions: Applications hosted by devices should be able to set up end-to-end secure (confidential, authenticated, and timely) communication channels.
Authenticity of application objects: Each application should be able to authenticate and determine the trustworthiness of its remote communicating principals. Note that even if a device is trusted, not all of its applications may be trusted to generate/access certain data blocks.
User authentication: The system should ensure that the medical staff and patients are properly identified before granting the appropriate level of access.
Access control of application data: The system should provide granular access control to application data blocks to enable clinicians and patients to retain control as well as record access to those data blocks.
Timely and secure logs: Security events anywhere in the stack may generate logs at the application layer, depending on the applicable policy. Those logs should be timestamped and transmitted to a central repository with minimum delay to enable both reconstruction of past events and estimation of likelihood of future events. Once generated, logs should be immutable and maintain accountability for log access.
Alerts for unexpected behavior (cross-layer): The system should support the generation and delivery of alerts based on local policy. Alerts generated at each layer of the communication stack may be reported up to the next layer, or directly to the application layer for logging and/or user notification.
Device provisioning and management (cross-layer): The system should support binding of devices to a facility-local trusted keying infrastructure to track their life cycle, ensuring revocation when required.
User management (cross-layer): The system should enable the management of users interacting with the devices within the system including addition and deletion of new and old users.
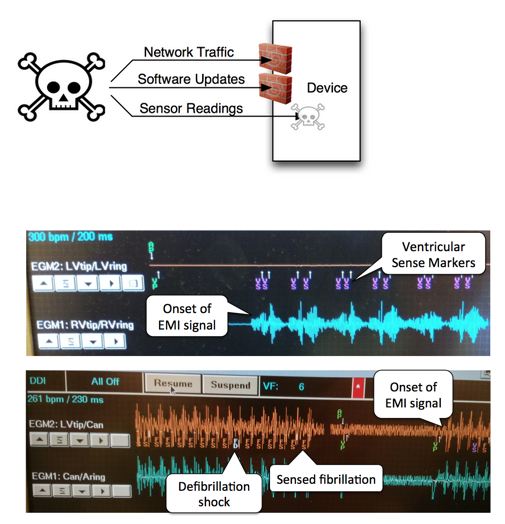
Improving the security of analog sensors
The measurement of physiologic processes is a central part of the functionality of medical devices. Some of those signals can be low and require amplification. Before the amplification stage, that signal may be vulnerable to electromagnetic interference (EMI). While the electromagnetic compatibility of those devices due to “back-door” coupling under random and accidental models have been well studied, the injection of signals using low power intentional EMI has not been carefully studied yet. We have studied the feasibility of signal injection with intentional EMI, demonstrated that it is possible under carefully controlled conditions, and proposed defenses. Our next step is to investigate signal injection with high power EMI and quantify the associated risk to the patient.
Publications
Denis Foo Kune, John Backes, Shane Clark, Dan Kramer, Matthew
Reynolds, Kevin Fu, Yongdae Kim, and Wenyuan Xu Ghost Talk: Mitigating
EMI Signal Injection Attacks against Analog Sensors, In Proceedings of
the 34th Annual IEEE Symposium on Security and Privacy 2013. (To
Appear.)
Denis Foo Kune, Eugene Vasserman, Krishna Venkatasubramanian, Yongdae
Kim, Insup Lee. "Towards a safe Integrated Clinical Environment: A
communication security perspective", ACM MedCOMM: Workshop on Medical
Communication Systems 2012.



